https://www.xperience-group.com/news-item/edr-mdr-and-xdr-what-do-they-mean/
Technology companies love acronyms, this has been true since the inception of IT. Even by historical standards, the amount that exist now within the Cyber Security industry is phenomenal. As a customer, you needed to purchase Anti-virus (AV) and a few other items such as firewalls, anti-ransomware and so on; however, if you were to now look at Cyber offerings; you would be bombarded with an array of 3-4 letter acronyms.
The reality is that most organisations aren’t looking for a particular product or service, they want re-assurance and a technical team that is not only capable, but also operationally mature enough to protect their organisation. With no standard way to determine the components of say an “XDR” solution from one provider to another; the customer is left trying to interpret it.
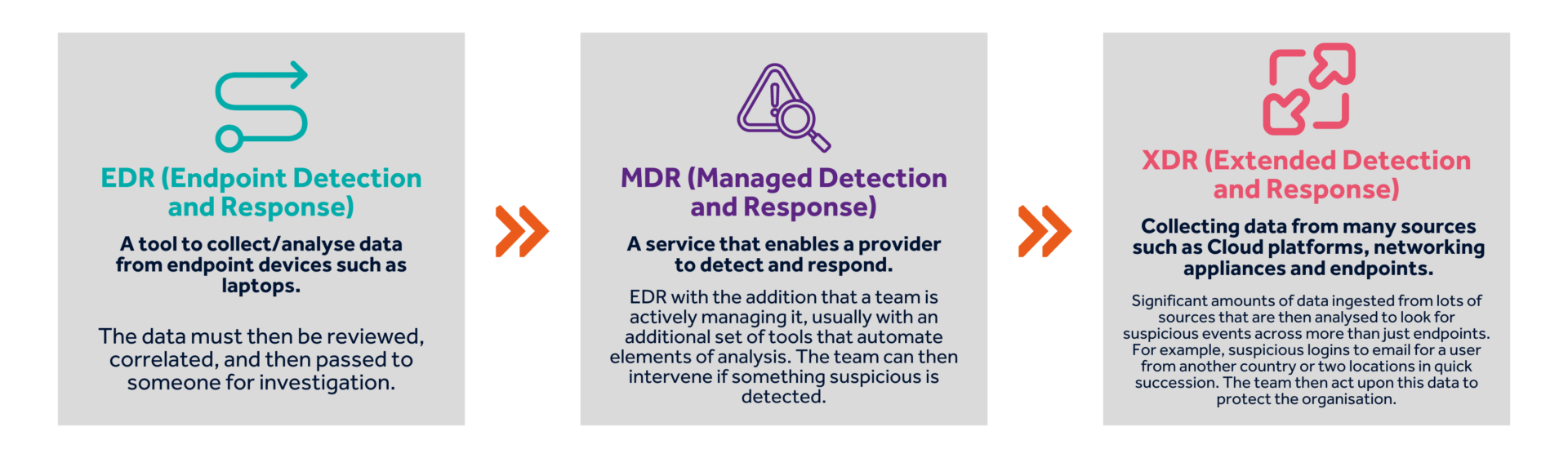
EDR & MDR have been around for a while, with most providers already incorporating the “XDR” pieces within their offering; however, with the industry now adopting this term; this has given license for an array of “new” product releases, services and so on. Whilst there is absolutely space in the market at the enterprise scale for these, it is important that we remain focussed that many non-enterprise organisations simply want a partner that will be identifying suspicious activity, intervening to prevent breaches and being transparent with any events that are captured.
I recently spoke with an experienced CTO who has been involved in many industries; including those that are either regulated or highly secured, with an impressive knowledge on all things IT. His comment was that Cyber is a totally different realm to “traditional IT”, it is such a specialist area that even with a talented team; he would partner with an organisation that really understands it – the risk of getting this wrong nowadays is just too high. He wouldn’t look for an EDR/MDR/XDR service – he would be looking for details on their track record of protecting organisations and whether they could become a team that felt like an extension of their own business.
We believe that if an organisation wants to partner for their cyber security protection, then the service should be all encompassing and data should be collated to enable this. Speak to our team and they won’t use jargon to describe what level of protection you receive; simply put we will make it simple to partner with us for full protection of your users and IT estate.
Want to learn more?